Recent Posts
Categories
Having all the cyber protection in place will help prevent many compromises. However, with the growing cybercriminal marketplace and community, you have to look at cyber incidents as a matter of when you will be breached, not if. This is why you need an incident response plan.
The longer it takes to respond to an incident the more damage it will cause. An incident response plan provides the steps that can be implemented to quickly respond and minimize the impact of a breach.
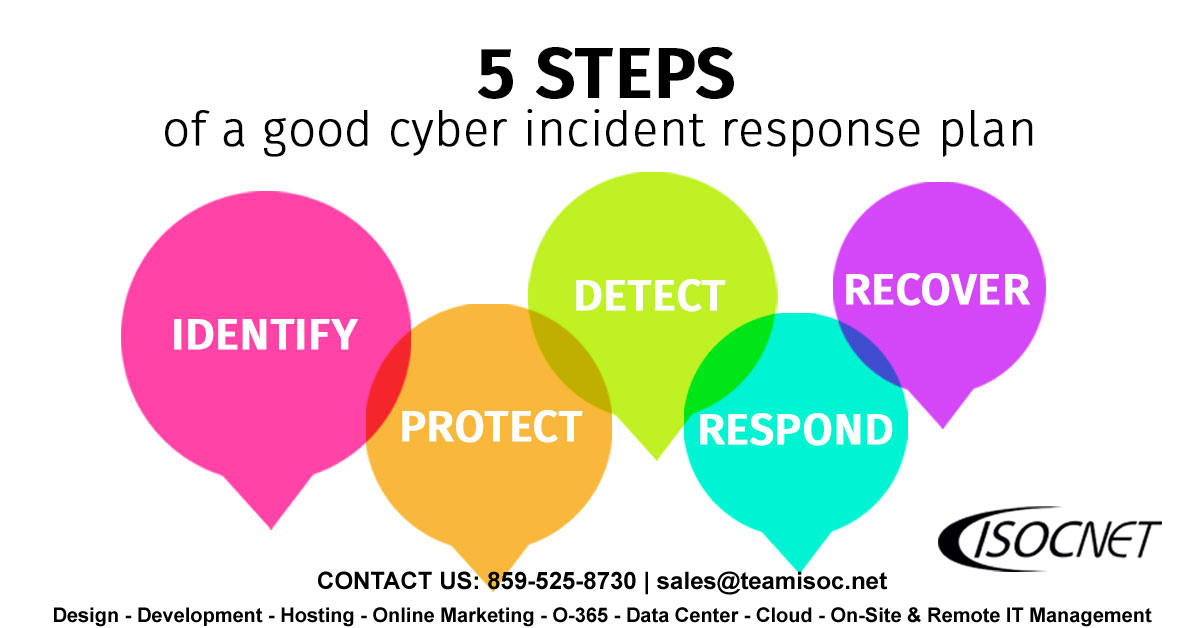
We recommend following the National Institute of Standards and Technology (NIST), incident response which has five phases. They are easy to follow and can allow your team proven steps to fall back on when implemented, tested, and updated properly.
Follow these five steps when implementing your Incident Response Plan.
Identify
Understanding what threats are out there will help you develop a way to protect your business, detect an attack, respond to it and recover from it. This framework does not only apply to cybersecurity, but security in general extending to people and processes.
To help you identify threats, you can start with known threats. Learn more about them in the Cyber Security Landscape. For your specific individual threats, you can also complete a vulnerability scan, risk assessment, review access & system logs, and track suspicious employee behaviors.
Protect
Once you understand the threats, having safeguards in place is critical to protecting your business. Each threat should be evaluated to determine the most appropriate action.
You can protect your business against cyberthreats by implementing security controls, firewalls, managing Access Controls, running Anti-virus programs, and training employees on security best practices. Read more about How to Protect your Business from Cybercriminals.
Detect
Since speed of responding from an incident correlates with impact, developing and implementing activities to detect a potential incident is critical.
Examples of tools to use to detect cyberthreats include Intrusion Prevention Software and Security Event and Incident Management (SEIM) Services. They monitor activity and alert you or take corrective actions to stop an infiltration.

Respond
This is where panic can set it in, but with a trusted, tried and true plan, you will minimize impact. This plan should include containment/isolation, analysis, mitigation, communications, and remediation.
Some things to consider in your plan is containing the breach and cutting it off to other systems, understanding what it is, what it has impacted, corrective action, along with a full analysis for preventive measures.
Recover
Getting business (or maybe just a user) back to full productivity as soon as possible is the goal, which includes restoring services. In additional, this may be where you look at what improvements need to be made to prevent this from happening again.
Your recovery may include restoring from a backup, adding additional securities, training employees on new securities, and communicating with necessary affected entities.
A solid Incident Response Plan can be the difference between an hour of downtime and going out of business. Security is a must have in today’s digital world. With that comes a well thought out, tested, and updated Incident Response Strategy. While this can be involved, you don’t have to go at it alone.



